Internet of Things – Secure and Segment Your Network

The Internet of Things (IoT) is rapidly gaining strength in the tech market space. As quickly as developers create an IoT device or concept, they are gobbled up by big business to enhance their portfolio of services and products to you. They can make life tasks easier, more convenient and – wait for it – they make your network less secure and vulnerable to the bad guys/girls whose goal is to disrupt your life, steal from you or hold you digitally hostage. With the proper IT services, there is nothing to worry about.
What to do?
There are several key technical concepts that ION Technology Group recommends you understand b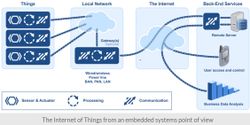 efore turning on your systems and making them available to you and sshhhhhh, the world. Let us follow the signal from soup to nuts. Review this graphical representation of the signal from https://www.micrium.com. Their illustration is spot on.
efore turning on your systems and making them available to you and sshhhhhh, the world. Let us follow the signal from soup to nuts. Review this graphical representation of the signal from https://www.micrium.com. Their illustration is spot on.
Remotely Turn on a Light at Your Office
- You make a request from your phone to turn on a light. This request is sent to a cluster of servers for which you have signed up for service
- The request is further sent through the Internet
- The request is received by your local network
- And in turn, the request is sent to your light sensor. Shazam! Your light accepts your request and turns on. Cool, huh?
Let us Restate the Above With Some Reality.
- You make a request from your phone to turn on the light. The request is sent to a cluster of servers that you hope are being managed, monitored, kept up-to-date and have no vulnerabilities, every second of every day. Does the recent Facebook data collection issue ring a bell? The Facebook issue could easily be your service for which you trust
- That request goes through the Internet to all the various routers for which you once again wonder, are these devices secure and have my best interest in mind
- It finally makes it to your home network that you have not updated since the day you pulled it out of the box and performed the setup
- And finally, it makes it to your light
Yes, you do have some control with the events that are taking place and where you have control, make sure you do your part. Two task are very easy and the other, well, maybe not so much.
- Make sure you update router’s vulnerabilities through firmware updates. If it is a home-class router within your business, you will find a section within that allows you to download and/or update your router’s firmware version. These updates are distributed to protect you and security vulnerabilities that have been discovered.
- Change the default username and/or password for your router. If you have already done this, you get a get a gold star.
- Segment your network and place your IoT device(s) on another network. Within business-class routers, this is a standard service. If you are using a home-class router, it may be provisioned for this kind of service and it may not.
It is simply too easy to hack the IoT world today as the goal of the manufacturer is to get these cool gadgets off their shelves and into your hands. And because of their approach, you need to take a different approach and ask yourself, “If I am hacked, what is my risk exposure?” Think about it. Using ION’s IT consulting services can save you a lot of headaches later.
If you are unsure of your setup or would like to have ION Technology Group perform a review of your configuration, please contact us. Let the experienced team at ION Technology Group in Voorhees, NJ, lend you a hand. They are the area’s premier resource, and their team provides expert maintenance and computer repair services for a wide range of router configurations. To learn more, call (856) 719-1818 to speak about service options tailored for your needs.
About the Business
Have a question? Ask the experts!
Send your question

